By Vadym Chernysh, Head of the CENSS Governing Council, Minister for Temporarily Occupied Territories and Internally Displaced Persons of Ukraine (2016-2019)
In today’s globalized world, individual states and groups of states that have formed alliances are struggling to compete with each other, primarily for access to markets and resources.For millennia, the war was one of the ways to achieve dominance and advantages. After two devastating world wars, humanity has established global peace and security systems to prevent states from resorting to war as a means for achieving their goals.
Despite the fact that global peace and security systems created after the two devastating world wars are in crisis, it is exactly for the reason of their existence that countries mainly refrain from waging full-scale wars.
Third Option
In order to achieve the desired result, countries often choose the so-called “third option”, that is, the kind of influence, which is carried out by conducting a wide range of covert operations on the territory of the target country in non-military spheres: political, economic, informational and others. The covert aspect of operations is important, in case of international complications, for “plausible denial” of the fact of interference in matters of another country, thus avoiding responsibility.
“Ladder” of covert operations¹
Carrying out covert operations in non-military operations may result in:
- having authorities of the target country adopt decisions needed for purposes of the influencing that country;
- coming to power in the target country of political forces or individuals loyal to the influencing country, enabling the partial loss of the state sovereignty;
- total loss of the state sovereignty as a result of being absorbed into the state that exerted influence.
Among better known successful examples of the above – when ruling regimes changed as a result of a wide range of covert operations in target countries, one may recall Iran (1953) and Guatemala (1954). In both countries, the CIA, which is not a military authority and is not under military command, was responsible for carrying out such operations.
Features That Define Hybrid Nature of a Conflict
At the same time, certain countries exercise open diplomatic, legal, economic and other influence, combining it with covert operations in non-military and military spheres. And in some cases, their military personnel are secretly engaged in hostilities on the territory of the target country.
It is this mix of various components – open and covert non-military with covert military ones, regardless of their specific proportion, – that serves as the main feature of the hybrid conflict.
At the very least, this raises two important questions.
First of all, carrying out of military action by military personnel of one country against the other according to the UN Charter is possible only for the purpose of self-defence and in other cases related to threats to peace. However, lack of substantiated legitimate grounds for use of military power is precisely the reason for conducting covert military operations.
Secondly, a country that secretly uses its own military personnel as combatants, in case of their capture by an opposing side, can easily deny the fact of them being a part of its active military personnel. In this case, captured individuals may find themselves ineligible to be entitled to guarantees rendered under rules of international humanitarian law.
Paramilitary Operations vs. Covert Military Operations
Despite possessing external similarity and the common denominator of secrecy, paramilitary operations differ from purely covert military operations that are mainly carried out directly by special operations forces (SOFs).
Their main difference is that the latter are conducted on the territory of the target country directly by foreign military personnel who carry out various combat tasks that cannot be carried out by traditional military means.
Instead, paramilitary operations are carried out without recruiting foreign military personnel as combatants. In such cases, the role of foreign personnel responsible for paramilitary operations is to train, provide material and informational support to local forces, and provide them with guidance and organizational assistance. Military actions, however, are carried out only by local forces.
Direct use of SOFs, the already mentioned risks notwithstanding, has its advantages. SOFs ground troops are professional military personnel, unlike local forces, who are mainly staffed with people from other professions that have undergone appropriate retraining.
Command and control system in regular military formations is far superior to that of local forces. Training of local forces for paramilitary operations (military exercises, supplies, etc.) takes a certain amount of time, whereas SFOs can be deployed within hours of the decision.
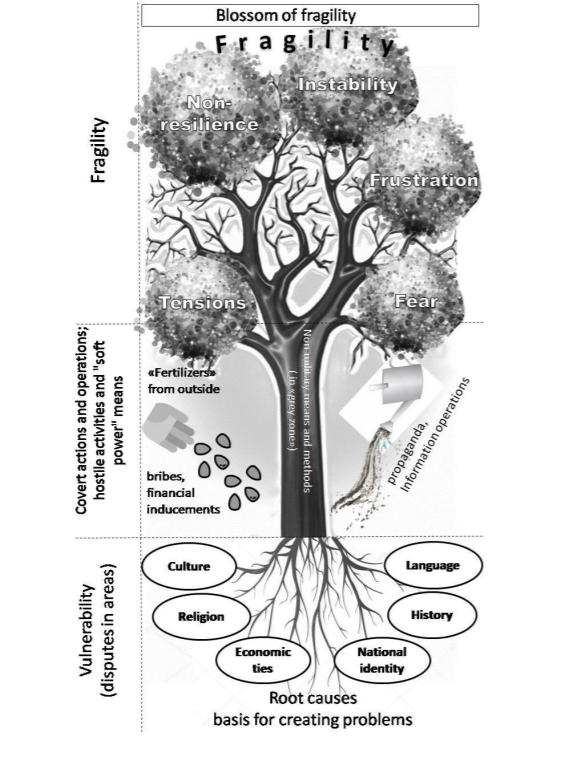
State of “Fragility”
No covert operation, whether military or non-military, is initiated without preparation. For these
purposes, the target country is carefully studied with a focus on internal problems.
Identification of disputes (so-called “root causes”) in political, economic, cultural, social and
other areas of the target country’s society is an important element in preparation for strategic planning of a comprehensive set of necessary measures and their intensity.
If these measures succeed, the target country’s society becomes fragile, which makes it an easy
target and jeopardizes its very existence.
For purposes of exerting influence on the target country, having a common border, common history, similar culture, religion, language, national origins, etc. is an obvious advantage.
“Soft Power”
Countries usually rely on three main types of power.
Military power, a variation of “hard power”, is channelled through intimidation, direct use, or threat of use of force to achieve desired goals.
Economic power, also a “hard” power, straightforward in its essence, may consist of freezing assets, sanctioning, providing economic incentives, preferences and bribery.
“Soft” power is the ability to influence actions, behaviour or value paradigms of others indirectly, without using coercion or material incentives, due to other types of motivation.
For example, creating an atmosphere of acceptance/non-acceptance of the appearance of a person can influence his/her decision regarding the purchase of everyday clothes.
At the level of states, as collective subjects, it can be manifested in the fact that similarity of musical, cinema, literary, sports, and other preferences of the population may influence even political decision-making by authorities of such states.
Countries’ “soft” power has several sources, including the cultural sphere (attractive to others), values (which are shared by others), and behaviour in the international arena (legitimacy and moral authority).
Sometimes, a change in value paradigms and benchmarks of a society leads to a change of political regimes.
A number of governments spend billions of dollars promoting national sports around the world, arranging various cultural events, advancing national cuisine, etc.
A number of countries also widely use entire “constellations” of non-governmental organizations to change value systems in other countries, initiate transformation processes in them, and as a consequence, positive changes in relations between them.
The best way to counter external influence is a skilful and timely amalgamation of all three of these types of power. Such a combination is sometimes called “smart power”.
Systems of Early Warning and Early Response
In order to identify potential threats in political, economic, cultural, social and other spheres that may be used by an opponent to destabilize the situation making it “fragile”, as well as actions already taken against the country for the same purpose, it is expedient and logical to create an early warning and early response system.
Such systems not only help to identify threats but also to swiftly react to them. They are based on the collection of information from open and closed sources, its analysis, and use of existing databases. These systems need to be properly constructed for timely detection of threats and, most importantly, for rapid response.
Of particular importance is the ability of relevant authorities to conduct counter-intelligence activities with a combination of traditional and relatively new methods.
Prevention of and protection against hybrid threats can only be successful if the central government, regional and local authorities, as well as bodies of local self-government, private sector and civil society participate in such activities.